Industrial cybersecurity (ICS) stands at the crossroads of technology, safety, and operational continuity, forming a critical pillar of modern manufacturing and industrial environments. As organizations embrace digital transformation and integrate advanced technologies such as IoT, cloud computing, and artificial intelligence, the need to secure these systems has never been more urgent. ICS cybersecurity is not just about preventing data breaches—it's about safeguarding production processes, protecting intellectual property, ensuring worker safety, and maintaining public trust.
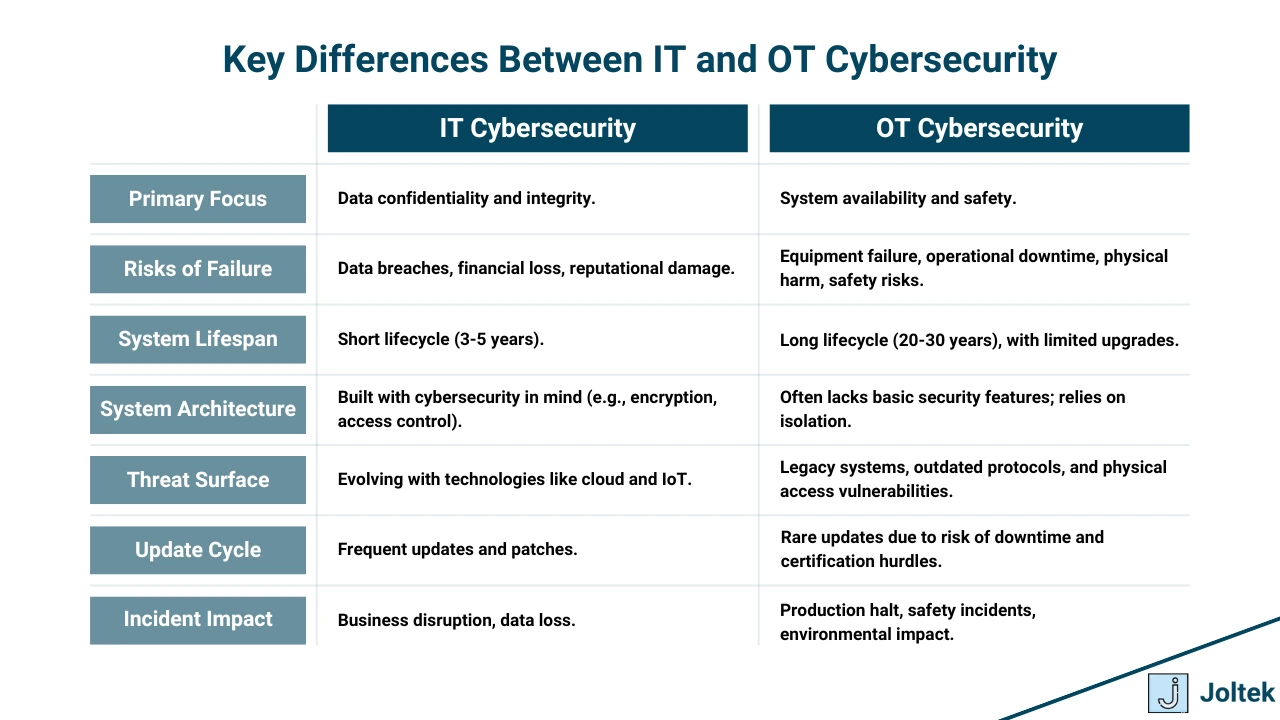
Unlike traditional IT systems, where the primary focus is on protecting data confidentiality and integrity, ICS cybersecurity prioritizes availability and safety. The stakes are exceptionally high: a cybersecurity breach in an industrial setting can lead to physical consequences, such as equipment failure, environmental damage, or even threats to human lives. From oil refineries to pharmaceutical plants, any disruption in industrial operations can have cascading effects on supply chains, economies, and communities.
Recent high-profile incidents, such as the Colonial Pipeline ransomware attack, have demonstrated the vulnerabilities of industrial environments and their potential for large-scale impact. These events underscore the importance of proactive measures to secure industrial control systems, which are increasingly connected to corporate IT networks and exposed to evolving threats.
ICS environments face unique challenges that set them apart from traditional IT systems:
Cybersecurity plays a pivotal role in enabling these advancements as industries undergo digital transformation, adopting smart manufacturing, cloud platforms, and advanced analytics. Without robust security measures, the benefits of digital transformation—efficiency, scalability, and real-time insights—are overshadowed by the risks of cyberattacks.
ICS cybersecurity is no longer just an IT concern; it’s a business imperative. Forward-thinking organizations view cybersecurity as an enabler of innovation and a competitive advantage. By prioritizing security, manufacturers can confidently embrace new technologies, meet regulatory requirements, and build trust with their customers and stakeholders.
In the sections that follow, we will explore the multifaceted world of ICS cybersecurity, delving into best practices, standards, and strategies to navigate this complex and ever-changing landscape.
Industrial cybersecurity (ICS cybersecurity) refers to the practice of protecting industrial control systems (ICS) and operational technology (OT) environments from cyber threats. These systems include critical infrastructure components such as Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), and Programmable Logic Controllers (PLCs). ICS cybersecurity aims to safeguard the operational processes that underpin industries such as manufacturing, energy, water, transportation, and healthcare.
Unlike traditional IT cybersecurity, ICS cybersecurity prioritizes the physical processes and equipment that drive production and service delivery. The goal is not just to prevent unauthorized access but to ensure continuous operations, protect worker safety, and maintain the integrity of physical assets.
In traditional IT cybersecurity, the CIA triad—Confidentiality, Integrity, and Availability—forms the foundation:
In OT and ICS environments, however, the priorities shift to availability and safety:
Confidentiality, while important, takes a backseat to these operational imperatives. The failure to prioritize availability or safety could lead to catastrophic outcomes, such as plant shutdowns, chemical spills, or even loss of life.
Historically, industrial control systems were isolated, or "air-gapped," from external networks. This physical separation provided a natural layer of security, as attackers could not access ICS without direct physical interaction.
The traditional ICS setup:
However, the landscape began to shift with the advent of:
While these advancements enable operational and business improvements, they also increase the attack surface, making ICS cybersecurity a critical priority in today's interconnected industrial environments.
The evolution from air-gapped systems to fully connected environments underscores the importance of adapting cybersecurity practices to the unique needs of ICS. In the next sections, we will explore standards, best practices, and strategies to protect these critical systems in the face of evolving threats.
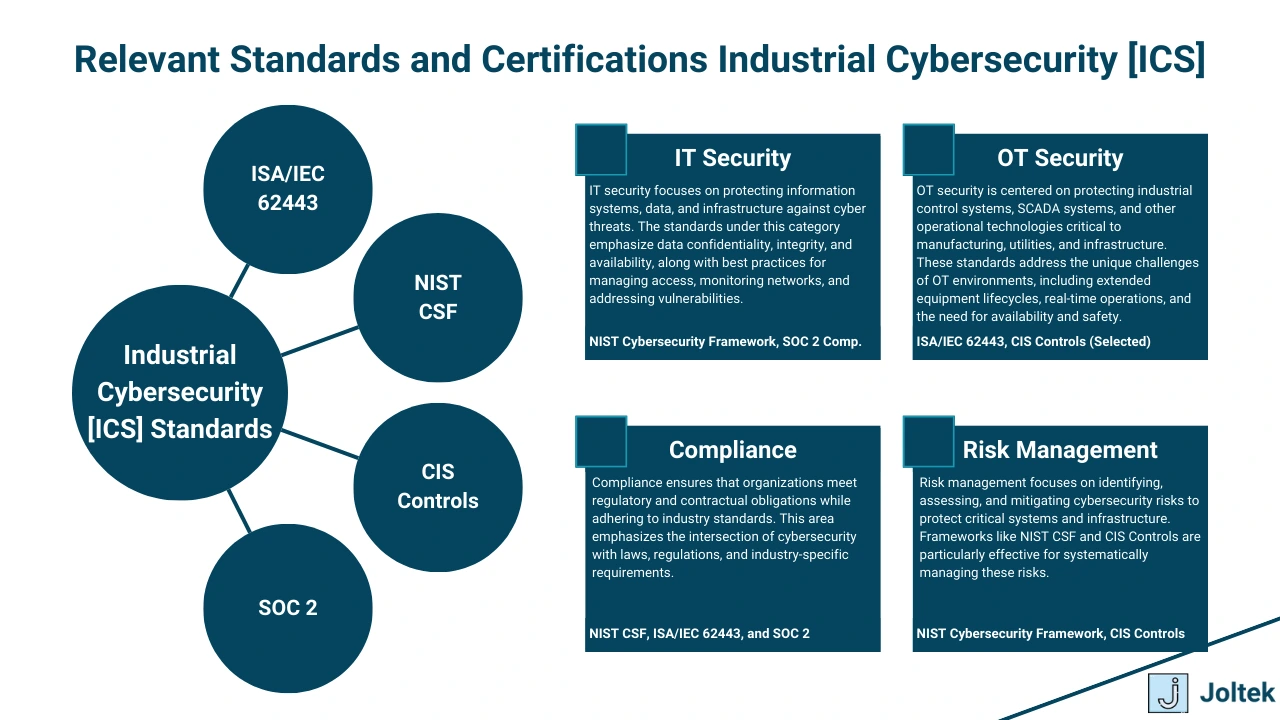
In industrial cybersecurity, standards and certifications play a pivotal role in guiding organizations toward secure practices, ensuring resilience, and maintaining trust with stakeholders. However, as Jason Waits from Inductive Automation emphasizes, compliance alone does not equate to robust security. The ultimate goal is to build strong security systems, with compliance as a natural byproduct of effective engineering. Below is an overview of key standards and certifications relevant to ICS cybersecurity.
ISA/IEC 62443 is a globally recognized standard specifically designed for industrial automation and control systems (IACS). It provides a comprehensive framework for securing ICS environments and is applicable to vendors, integrators, and end users.
Key elements include:
ISA/IEC 62443 is critical for ICS environments due to its focus on operational technology (OT) systems, making it a cornerstone for organizations aiming to secure their industrial processes.
The NIST Cybersecurity Framework (CSF), developed by the National Institute of Standards and Technology, provides a flexible and widely adopted framework for managing cybersecurity risks.
Key components:
While not ICS-specific, NIST CSF is highly applicable in environments where IT and OT converge. It is often used as a baseline for developing cybersecurity programs in industrial sectors.
The Center for Internet Security (CIS) provides a set of best practices designed to enhance cybersecurity across all sectors, including ICS.
Key resources include:
For smaller organizations or those just starting their cybersecurity journey, the CIS Controls offer a practical, scalable approach to achieving security maturity without overwhelming complexity.
Service Organization Control 2 (SOC 2) is an auditing standard for organizations managing data and providing services, focusing on:
SOC 2 is particularly beneficial in the sales cycle, as customers often seek assurance that a vendor follows rigorous cybersecurity practices. Achieving SOC 2 compliance can enhance credibility and trust.
While certifications and standards provide a roadmap, they are not a substitute for real security. As Jason Waits emphasizes:
Key Takeaway: Effective cybersecurity focuses on reducing real-world risks through proactive engineering, regular audits, and continuous improvement. Compliance should follow naturally as a byproduct of these efforts.
By aligning with these standards and certifications, organizations can establish a robust cybersecurity foundation. However, true resilience comes from combining these frameworks with a security-first mindset, ensuring that both compliance and practical security measures are fully integrated into day-to-day operations.
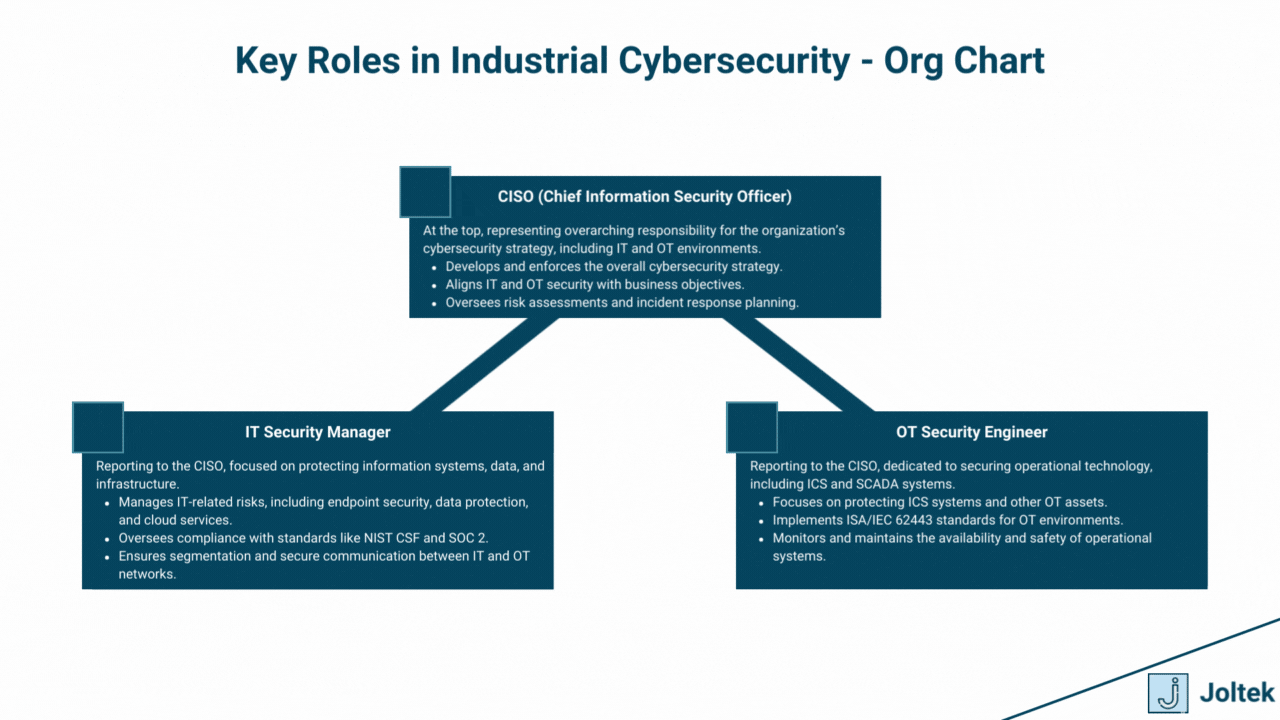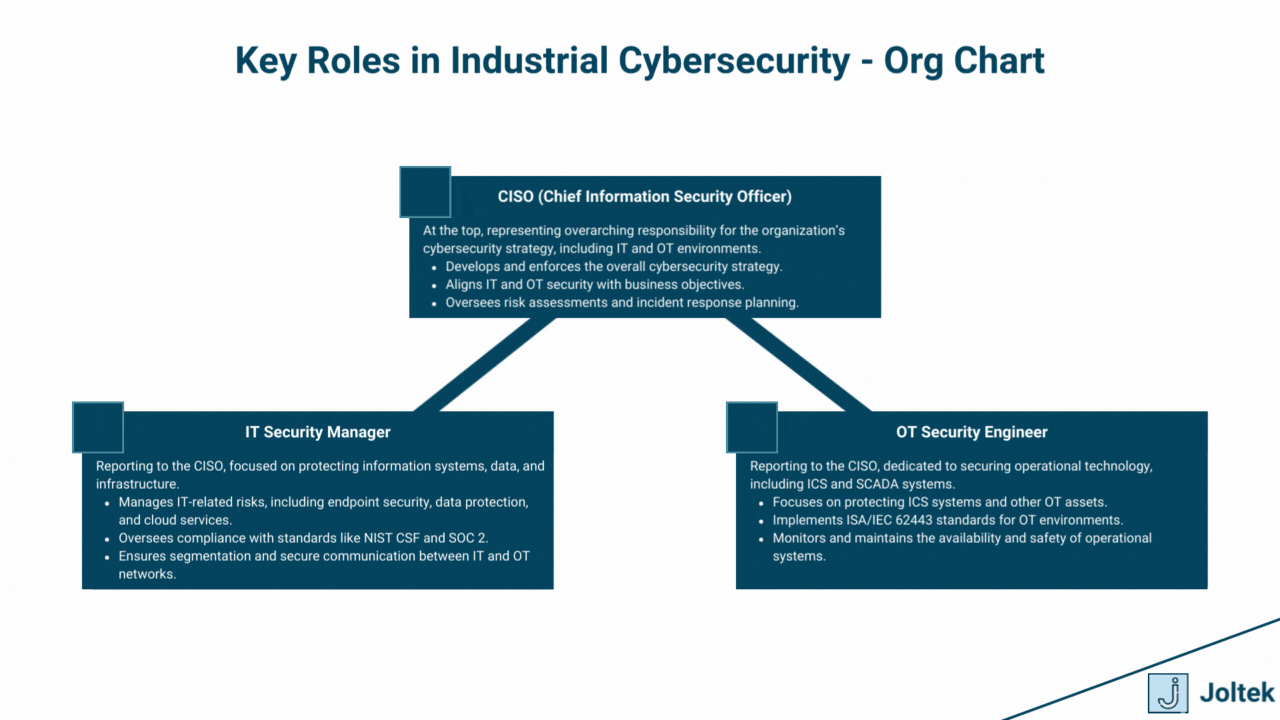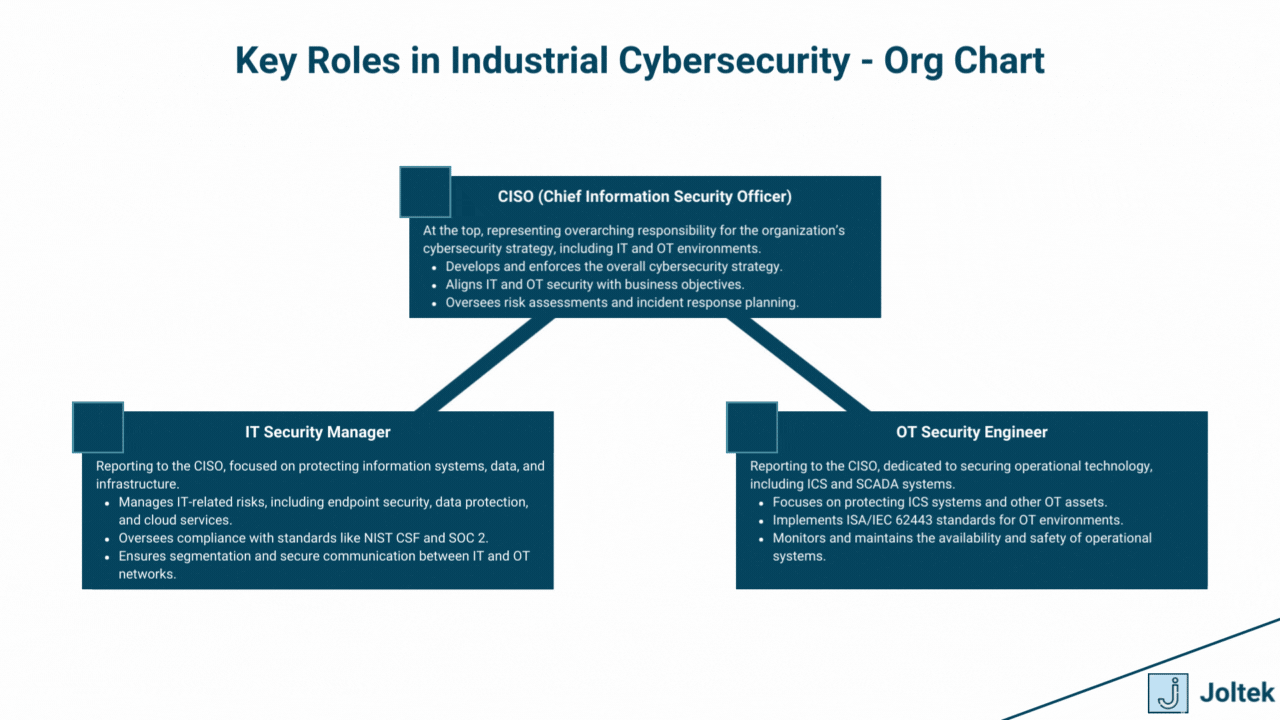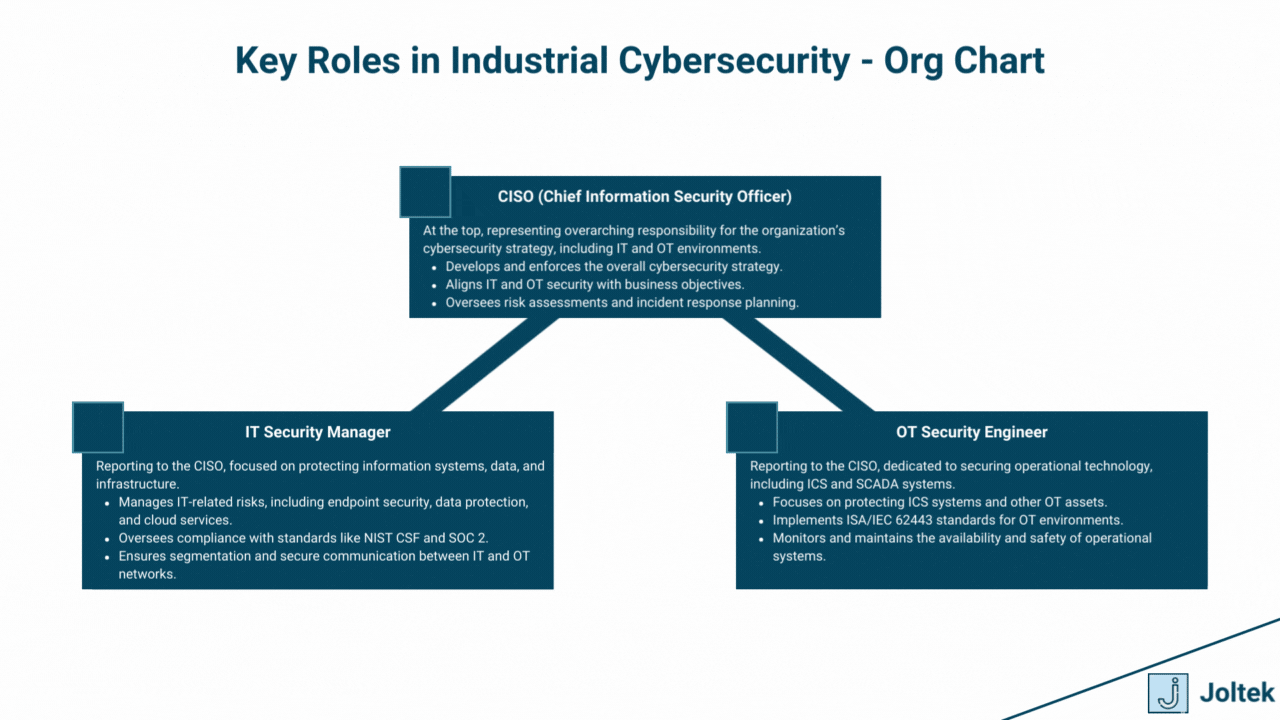
The convergence of IT and OT environments requires close collaboration between traditionally siloed teams. Bridging this gap is critical for ensuring comprehensive cybersecurity coverage.
A strong security culture is the foundation of effective ICS cybersecurity. It ensures that all employees, from the plant floor to the C-suite, understand their role in protecting critical systems.
By aligning roles, fostering collaboration, and prioritizing cultural change, organizations can create a resilient foundation to protect their industrial control systems against evolving cyber threats.
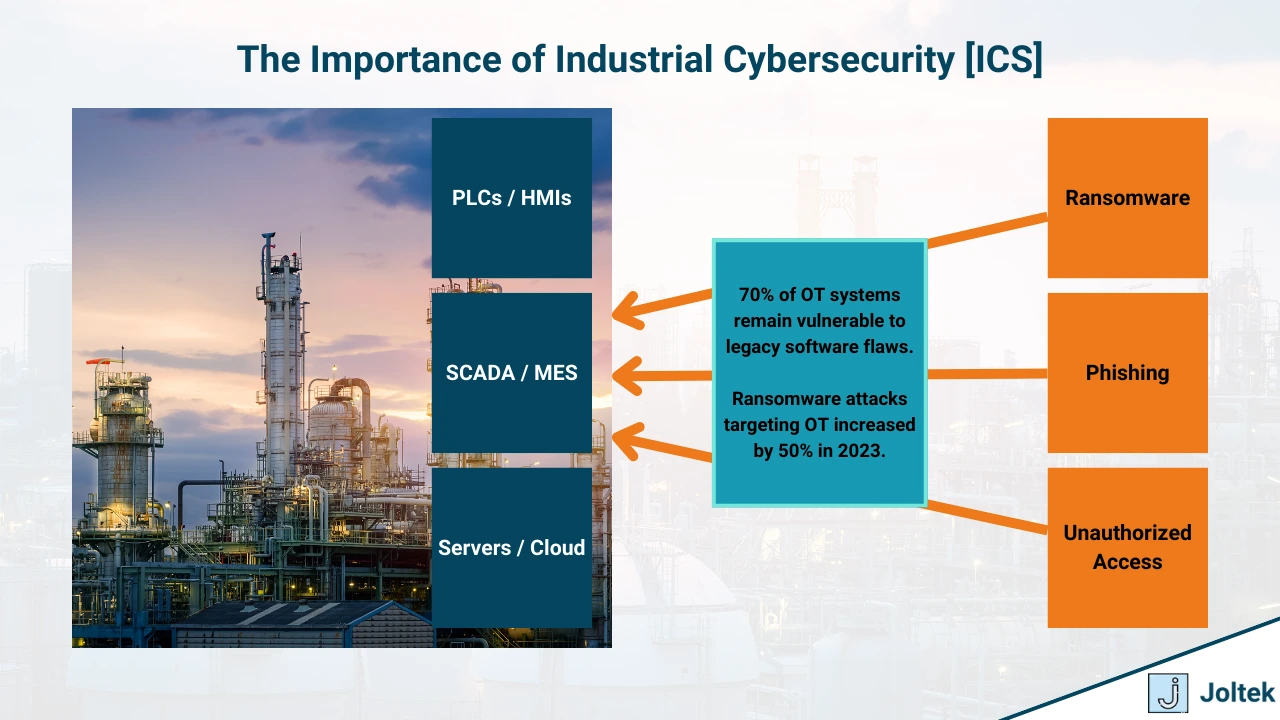
The threat landscape for industrial control systems (ICS) is both complex and rapidly evolving. These systems are responsible for managing critical infrastructure and industrial processes, making them high-value targets for cyberattacks. The unique vulnerabilities of ICS systems, combined with their operational importance, make understanding and addressing these threats essential for organizations worldwide.
One of the most significant challenges is the reliance on legacy systems, such as Windows XP or Windows 7. These platforms, often still in use, no longer receive security updates. Designed for reliability rather than modern security, these systems are highly susceptible to exploitation, yet replacing or updating them is often deemed too disruptive or costly.
Industrial protocols also pose a serious risk. Many, such as Modbus and DNP3, were designed for interoperability and simplicity, not security. They frequently operate without encryption or authentication, exposing sensitive data to interception or manipulation. This lack of built-in security creates persistent vulnerabilities across industrial networks.
Attackers leverage a variety of methods to exploit these vulnerabilities.
Real-world incidents illustrate the devastating potential of these vulnerabilities:
As organizations adopt cloud services, IoT devices, and remote access tools, the attack surface continues to grow. These technologies enable efficiency and innovation but introduce new entry points for cyber threats, demanding increased vigilance and robust defenses.
Addressing this threat landscape requires a multifaceted approach, balancing technical defenses, such as patch management and network segmentation, with proactive measures to mitigate human error. In the next section, we’ll explore best practices for securing ICS environments against these evolving challenges.
Securing Industrial Control Systems (ICS) demands a comprehensive approach that balances technical defenses, operational considerations, and proactive planning. Given the high stakes associated with ICS environments—ranging from operational downtime to safety risks—adopting best practices is essential for mitigating threats and ensuring resilience. Below, we explore key strategies for robust ICS cybersecurity.
A strong cybersecurity foundation begins with understanding the systems in your environment. Maintaining an accurate and up-to-date inventory of all assets, including hardware, software, and network devices, is crucial. This inventory should encompass both IT and OT systems, highlighting their configurations, roles, and interconnections.
Equally important is establishing secure configuration baselines for these assets. Secure baselines serve as a benchmark, ensuring that systems adhere to organizational security policies. Tools like the CIS Benchmarks provide detailed, actionable guidelines for hardening operating systems, servers, and applications. Regular monitoring of configurations is essential to detect and address unauthorized changes, which may indicate a breach or vulnerability.
By implementing robust asset and configuration management practices, organizations gain visibility into their environment, enabling them to prioritize resources and secure critical systems effectively.
Network segmentation is a cornerstone of ICS cybersecurity, designed to limit an attacker’s ability to move laterally within an environment. By separating IT and OT networks using firewalls and demilitarized zones (DMZs), organizations can reduce the attack surface and better protect sensitive operational systems. Within OT networks, further segmentation based on system criticality—such as isolating safety systems from production lines—adds an additional layer of defense.
Access controls complement segmentation by ensuring that only authorized personnel can interact with ICS systems. Applying the principle of least privilege, where users have access only to the resources necessary for their role, helps minimize the risk of insider threats or compromised accounts. Multi-factor authentication (MFA) is particularly effective for securing remote access to systems, adding an additional layer of protection against unauthorized logins.
Combining segmentation and access controls provides a dual barrier that limits exposure and makes it more difficult for attackers to gain footholds or escalate privileges within the network.
Anticipating risks before they materialize is a critical aspect of ICS cybersecurity. Threat modeling is a systematic process that helps organizations identify vulnerabilities and assess potential attack scenarios. Frameworks like STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) or DREAD (Damage, Reproducibility, Exploitability, Affected Users, Discoverability) provide structured approaches for evaluating threats.
The process typically involves gathering cross-functional teams to analyze the architecture of ICS systems and simulate hypothetical attack scenarios. By walking through how an attacker might exploit a vulnerability, teams can identify weaknesses and prioritize mitigation efforts.
Regularly revisiting and updating threat models ensures that they remain relevant as the environment evolves. This proactive practice enables organizations to build security into their systems rather than reacting to incidents after they occur.
Being prepared for cybersecurity incidents is just as important as preventing them. A well-defined incident response plan provides a roadmap for detecting, containing, and recovering from potential breaches. This plan should outline roles and responsibilities, specify escalation paths, and include clear communication protocols for internal teams and external partners.
Tabletop exercises are a practical way to test and refine these plans. During these exercises, participants simulate scenarios such as ransomware attacks, system outages, or compromised ICS devices. These exercises not only identify gaps in the response plan but also help build confidence and coordination among team members.
Effective incident response planning minimizes downtime, reduces the impact of incidents, and ensures compliance with industry regulations. It also demonstrates to stakeholders that the organization takes cybersecurity seriously.
While patching is a fundamental cybersecurity practice, it poses unique challenges in ICS environments. Many industrial systems operate on extended lifecycles, and downtime for patching can disrupt production. Despite these challenges, a proactive approach to patch management is essential.
Organizations should develop a patching strategy that includes thorough testing in non-production environments and scheduling updates during planned maintenance windows. For systems where patching is not feasible, virtual patching technologies, such as intrusion prevention systems (IPS), can provide an interim defense by shielding vulnerabilities from exploitation.
Coordinating closely with vendors is also vital for staying informed about known vulnerabilities and available updates. Regular patching ensures that systems are protected against known exploits, significantly reducing the risk of compromise.
Implementing these best practices provides a holistic defense against the unique challenges of ICS cybersecurity. Asset and configuration management establishes visibility and control, while network segmentation and access controls reduce the likelihood of successful attacks. Threat modeling and incident response planning equip organizations to anticipate and respond effectively to threats, while proactive patching addresses vulnerabilities before attackers can exploit them.
In ICS environments, where downtime and disruptions can have far-reaching consequences, these strategies are not optional—they are essential for safeguarding critical systems and ensuring operational resilience.
Vendors and Original Equipment Manufacturers (OEMs) play a pivotal role in the cybersecurity landscape of Industrial Control Systems (ICS). Their responsibilities extend beyond product development to include ongoing support, security enhancements, and collaboration with end-users to ensure robust protection of critical infrastructure.
Vendors are tasked with several key responsibilities to enhance the security posture of ICS environments:
By fulfilling these responsibilities, vendors help ensure that their products remain resilient against evolving cyber threats.
Operational Technology (OT) environments often feature equipment with extended lifecycles, sometimes spanning decades. This longevity presents unique challenges:
Addressing these challenges requires a strategic approach, balancing the need for security with operational continuity.
Inductive Automation exemplifies proactive vendor engagement in cybersecurity through several initiatives:
Through these efforts, Inductive Automation demonstrates a comprehensive commitment to enhancing the cybersecurity resilience of its products and supporting its customers in maintaining secure ICS environments.
The rapid adoption of advanced technologies is reshaping the cybersecurity landscape for Industrial Control Systems (ICS). While innovations such as artificial intelligence (AI), cloud computing, and IT/OT convergence offer new opportunities for enhanced security and efficiency, they also introduce new risks and challenges. Understanding these emerging trends is essential for organizations seeking to secure their industrial environments while leveraging the benefits of modern technology.
Artificial intelligence is increasingly being used to improve cybersecurity, providing powerful tools for threat detection and response. AI-powered systems can analyze vast amounts of data in real-time, identifying unusual patterns or behaviors that might signal an attack. For example, machine learning algorithms are particularly adept at spotting anomalies in network traffic, making it easier to detect insider threats or sophisticated cyberattacks that evade traditional defenses.
AI is also transforming incident response by automating many routine tasks. It can prioritize alerts, suggest remediation steps, and even take immediate defensive actions, such as isolating a compromised device from the network. Additionally, predictive analytics driven by AI can help organizations anticipate potential vulnerabilities and preemptively address them before they are exploited.
However, the same technology that enhances security can also be exploited by attackers. Cybercriminals are already using AI to craft highly convincing phishing emails and develop adaptive malware capable of evading detection. By analyzing public data, such as social media profiles, attackers can use AI to personalize phishing attempts, making them more effective. The dual-use nature of AI presents a growing challenge, as defenders must continuously innovate to stay ahead of adversaries.
Cloud computing is becoming an integral part of industrial operations, offering capabilities such as remote monitoring, centralized data storage, and advanced analytics. For many organizations, cloud adoption enables greater scalability and agility, allowing them to integrate cutting-edge technologies and streamline processes.
From a security perspective, the cloud provides centralized tools for managing access controls, monitoring activities, and detecting threats across distributed systems. These capabilities make it easier to secure large-scale environments, especially as the number of connected devices continues to grow.
However, cloud adoption also introduces new risks. Misconfigured cloud environments remain one of the leading causes of data breaches. Moreover, as industrial data is moved to third-party platforms, organizations must address concerns about data privacy, regulatory compliance, and potential dependency on external vendors. The expanded attack surface created by cloud integration requires rigorous security protocols, including regular audits, secure configurations, and robust access control measures.
The integration of Information Technology (IT) and Operational Technology (OT) systems is revolutionizing industrial environments. This convergence enables real-time data sharing, predictive maintenance, and enhanced operational efficiency. For example, IT tools such as enterprise resource planning (ERP) systems can now directly interface with OT systems like PLCs, providing unprecedented levels of visibility and control.
While IT/OT convergence offers significant benefits, it also creates challenges. The blending of traditionally separate networks increases the overall attack surface, making it easier for threats to spread from IT systems into OT environments. Many legacy OT systems were not designed with security in mind, leaving them vulnerable when connected to IT networks. Additionally, the cultural differences between IT and OT teams—such as the focus on data security in IT versus system availability in OT—can complicate collaboration and create gaps in security.
To address these challenges, organizations must adopt a unified approach to cybersecurity. This involves fostering collaboration between IT and OT teams, implementing robust network segmentation, and developing shared security policies. Legacy systems must be assessed and secured, often through strategies such as virtual patching or controlled network access.
Emerging technologies are fundamentally transforming how ICS environments operate, providing opportunities for enhanced efficiency and security. However, they also require organizations to rethink their cybersecurity strategies. The introduction of AI, cloud computing, and IT/OT convergence comes with inherent risks, but with careful planning and proactive measures, these risks can be mitigated.
By embracing these trends with a focus on security, organizations can leverage the benefits of innovation while ensuring the resilience and safety of their critical systems. The future of ICS cybersecurity lies in balancing technological advancements with comprehensive risk management, creating a more secure and connected industrial landscape.
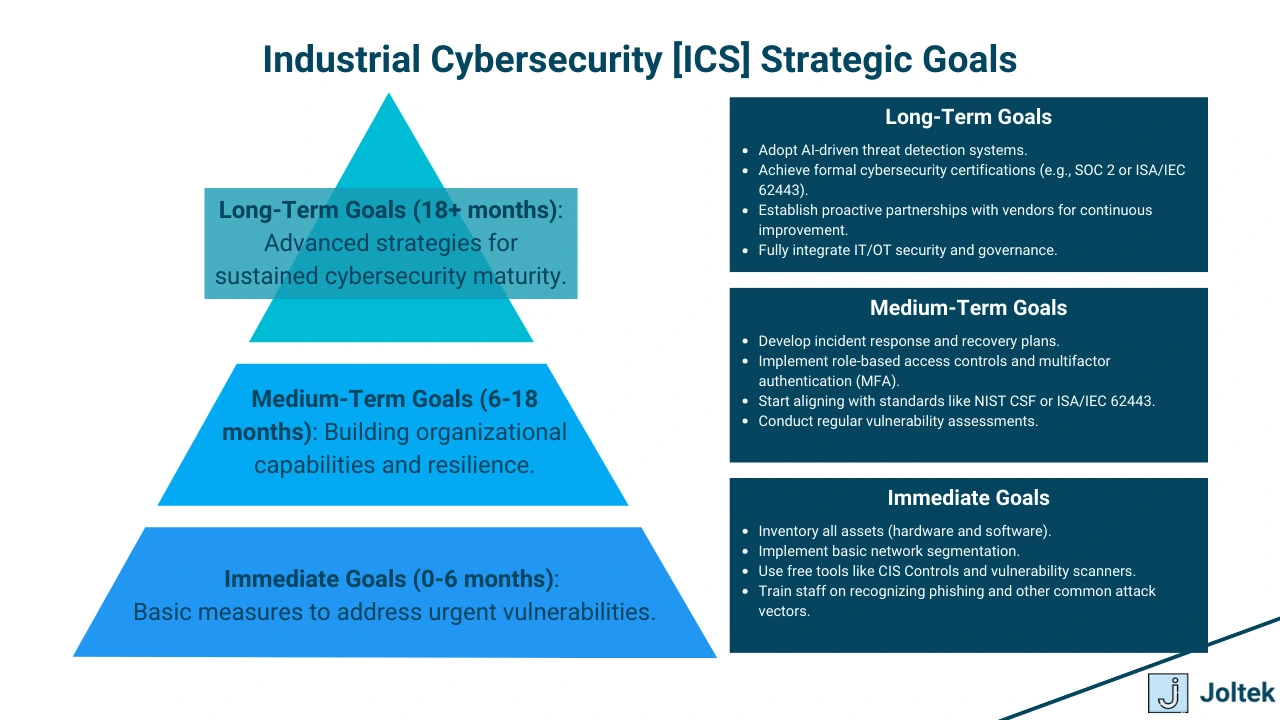
Improving cybersecurity in Industrial Control Systems (ICS) can seem daunting, especially given the complexity and critical nature of these environments. However, organizations can make significant progress by following a systematic approach. Practical steps, starting with fundamental practices like asset management and advancing toward long-term strategies, provide a clear path for strengthening defenses.
Effective cybersecurity begins with knowing what you need to protect. Creating and maintaining a comprehensive inventory of all assets—hardware, software, network devices, and systems—is essential. This inventory should cover both IT and OT environments, detailing the configurations, firmware versions, and interconnections of each asset.
Configuration baselines provide a standard for how systems should be set up to minimize vulnerabilities. These baselines ensure that all devices operate within secure parameters, preventing unauthorized changes that could introduce risks. Monitoring configurations continuously helps detect anomalies, such as unexpected modifications, which might indicate a breach or misconfiguration.
For organizations looking to enhance their cybersecurity posture without significant financial investment, leveraging free resources is a smart starting point. The Center for Internet Security (CIS) provides two valuable tools:
These resources are especially beneficial for smaller organizations with limited cybersecurity expertise. By following these proven frameworks, companies can achieve significant security improvements without extensive costs.
Achieving robust ICS cybersecurity is a journey that requires clear goals and a phased approach. Developing a roadmap helps organizations prioritize initiatives and allocate resources effectively.
A typical roadmap might include:
Organizations should regularly review and update their roadmap to account for evolving threats and technological advancements.
For smaller organizations, cost is often a significant barrier to implementing comprehensive cybersecurity measures. However, limited budgets do not mean security has to be compromised. Prioritization is key.
Start by addressing the most critical risks. For example, securing legacy systems with virtual patching or isolating them through network segmentation can be cost-effective. Using free or low-cost tools, such as open-source vulnerability scanners, provides additional protection without requiring significant investment.
Partnerships with vendors can also be invaluable. Many vendors offer resources like security hardening guides or provide insights into configuring systems securely. Leveraging vendor expertise can reduce costs while improving the organization’s overall security posture.
Improving ICS cybersecurity doesn’t require an all-at-once approach. By starting with foundational practices like asset management and leveraging free resources, organizations can make meaningful progress. Developing a clear roadmap ensures that efforts are aligned with long-term goals, while careful prioritization allows smaller organizations to balance cost and security effectively.
Taking practical, incremental steps not only builds a stronger defense against cyber threats but also fosters a culture of continuous improvement and resilience in the face of evolving risks.
In today’s industrial landscape, where cyber threats are increasingly prevalent, robust cybersecurity is no longer just a necessity—it’s a competitive differentiator. Organizations that prioritize security not only protect their operations but also build trust with customers, partners, and stakeholders. By positioning cybersecurity as a key aspect of their value proposition, businesses can gain an edge in the market while ensuring long-term operational resilience.
Customers and partners increasingly demand assurances that the organizations they work with can protect sensitive data and critical infrastructure. Demonstrating a strong commitment to cybersecurity can set a company apart, particularly in industries where trust and reliability are paramount, such as manufacturing, energy, and healthcare.
Businesses can use cybersecurity certifications, such as SOC 2 or ISA/IEC 62443, to validate their commitment to best practices. These certifications signal to customers that the company meets rigorous security standards, reducing the perceived risk of doing business. Additionally, incorporating security into marketing materials—such as highlighting the use of advanced technologies like threat detection systems or participation in initiatives like bug bounties—can further enhance a company’s reputation for reliability.
Transparency is a cornerstone of building trust in cybersecurity. Customers are more likely to choose a vendor or partner that openly communicates about its security measures and incident response processes. Sharing detailed information about compliance, regular third-party audits, and proactive vulnerability management fosters confidence that the organization takes security seriously.
Proactive communication also plays a critical role in maintaining trust during incidents. Companies that demonstrate transparency and a swift, effective response to breaches or vulnerabilities show stakeholders that they prioritize security and are prepared to handle challenges responsibly. A clear post-incident communication plan, combined with visible actions to address vulnerabilities, can even strengthen customer loyalty despite an incident.
Investing in a strong cybersecurity program delivers benefits that extend far beyond immediate protection against threats. Over time, a secure environment reduces downtime and operational disruptions, ensuring smoother production processes and higher overall efficiency. Preventing costly breaches also protects an organization’s financial health and reputation, which can be difficult to rebuild after a significant incident.
Cybersecurity also drives innovation by enabling companies to confidently adopt new technologies like cloud computing, AI, and IoT. Knowing that robust protections are in place allows businesses to pursue digital transformation initiatives without exposing themselves to undue risk.
Furthermore, organizations with strong security postures are better positioned to meet regulatory requirements and industry standards, avoiding potential fines and legal challenges. In a world where cybersecurity is increasingly scrutinized by regulators, proactive investment ensures compliance while minimizing exposure to legal and financial penalties.
By treating ICS cybersecurity as a strategic asset rather than a reactive expense, organizations can protect their operations and reputation while unlocking new opportunities for growth and innovation. Cybersecurity is no longer just a technical concern—it is a vital component of a company’s value proposition and a driver of sustained success.
The future of Industrial Control Systems (ICS) cybersecurity will be shaped by a convergence of escalating threats, evolving regulations, and the constant push for innovation. As industrial environments become more connected and complex, organizations must anticipate and adapt to new challenges while balancing operational efficiency with robust security.
Governments and regulatory bodies around the world are intensifying their focus on ICS cybersecurity. High-profile incidents like the Colonial Pipeline ransomware attack have highlighted vulnerabilities in critical infrastructure, prompting stricter regulations. In regions such as the European Union, frameworks like the Network and Information Systems (NIS) Directive and GDPR emphasize both cybersecurity and data protection, with penalties for non-compliance. Similarly, in the United States, initiatives like the Cybersecurity & Infrastructure Security Agency (CISA) and Executive Order 14028 on improving the nation’s cybersecurity are driving compliance efforts.
In the future, organizations can expect:
While these regulations aim to enhance security, they will also increase the burden on organizations, particularly smaller ones with limited resources. Companies that proactively align with these standards will find themselves better prepared to navigate regulatory demands and maintain trust with stakeholders.
Ransomware has emerged as a dominant threat in the cybersecurity landscape, and its impact on Operational Technology (OT) environments is becoming increasingly evident. Unlike traditional ransomware attacks targeting IT systems, attacks on OT networks threaten physical operations, safety, and even public infrastructure.
In the coming years:
The financial and operational stakes in OT ransomware attacks are far higher than in traditional IT breaches. Organizations must invest in incident response planning, network segmentation, and robust backup strategies to mitigate the impact of these attacks.
As industries embrace digital transformation, the adoption of technologies like AI, IoT, and cloud computing is accelerating. While these advancements promise greater efficiency, scalability, and insight, they also introduce new vulnerabilities.
Future trends include:
To navigate these challenges, organizations must adopt a balanced approach that prioritizes security alongside innovation. This includes embedding cybersecurity into the design of new systems, fostering collaboration between IT and OT teams, and continuously updating security strategies to keep pace with evolving threats.
The future of ICS cybersecurity will demand vigilance, adaptability, and a forward-looking approach. Organizations that embrace these principles will not only protect their critical operations but also position themselves as leaders in the increasingly digital and interconnected industrial world.
Industrial cybersecurity (ICS) is no longer a niche concern; it is a critical priority for organizations operating in an increasingly connected and digital world. Throughout this discussion, we’ve explored the complexities, challenges, and opportunities in securing Industrial Control Systems. From understanding the unique vulnerabilities of legacy systems to leveraging advanced tools like AI and cloud services, the path to robust cybersecurity requires a combination of strategic planning, technical measures, and organizational commitment.
Cyber threats are constantly evolving, making static approaches to cybersecurity ineffective. Organizations must commit to continuous learning, staying updated on emerging threats, new technologies, and industry standards. Regular training, threat modeling exercises, and investments in advanced tools are essential to keeping pace with the shifting threat landscape.
Building a resilient cybersecurity posture is not a one-time project—it is an ongoing process that requires vigilance, adaptation, and collaboration across teams and stakeholders.
For organizations operating in industrial environments, prioritizing cybersecurity is no longer optional. The stakes are too high—ranging from operational disruptions and financial losses to safety risks and reputational damage. By embedding cybersecurity into every aspect of their operations, companies can safeguard their critical systems, comply with regulatory demands, and position themselves as trusted partners in their industries.
Start by:
Industrial cybersecurity is not just a technical challenge; it is a strategic imperative. The organizations that succeed in this domain will not only protect their operations but also lead the way in a more secure and resilient industrial future. Now is the time to act.