Understanding how networks function is the foundation for anyone working in operations, engineering, or systems integration. Before we can design, secure, or optimize industrial systems, we need to step back and understand how devices talk to one another. The same way signals travel across your home network from your laptop to your router to the cloud, data flows across the factory floor. The difference lies in how we manage, protect, and scale that communication inside an operational environment.
In this article, we will expand beyond the video lesson to connect the dots between consumer networking and industrial networking. We will explore what makes a simple home network both powerful and limiting, and how those same principles evolve inside a manufacturing plant. This foundational knowledge helps build toward more advanced concepts such as VLANs, subnets, managed switches, and industrial firewalls.
A strong understanding of networking fundamentals is the single most important step toward mastering OT and industrial systems integration. It allows engineers and technicians to visualize how information moves between sensors, controllers, and higher level systems such as SCADA or MES. Once you see the structure, you begin to see where performance bottlenecks, communication gaps, and cybersecurity vulnerabilities emerge.
This is not a theoretical overview. It is a practical guide meant to help you recognize familiar concepts from everyday technology and apply them to industrial networks that demand higher reliability, tighter control, and stronger security. If you are new to these topics, start here, build confidence in the basics, and then continue exploring how these same principles scale within real production environments.
For a deeper look at how networking and data connectivity form the backbone of modern plants, read Unlocking Industrial Data in Manufacturing.
Every network, whether in your home or inside a production facility, follows the same essential principle. Information must move from one place to another in a structured and reliable way. Understanding how this flow happens on a small scale helps engineers appreciate the complexity of large industrial networks. A basic network is simply a pathway that allows devices to exchange information through clearly defined layers and components.
In homes, that pathway begins with your internet provider. On the plant floor, it begins with a carefully designed network boundary that separates operational systems from the outside world. The foundation is the same, but the implementation could not be more different.
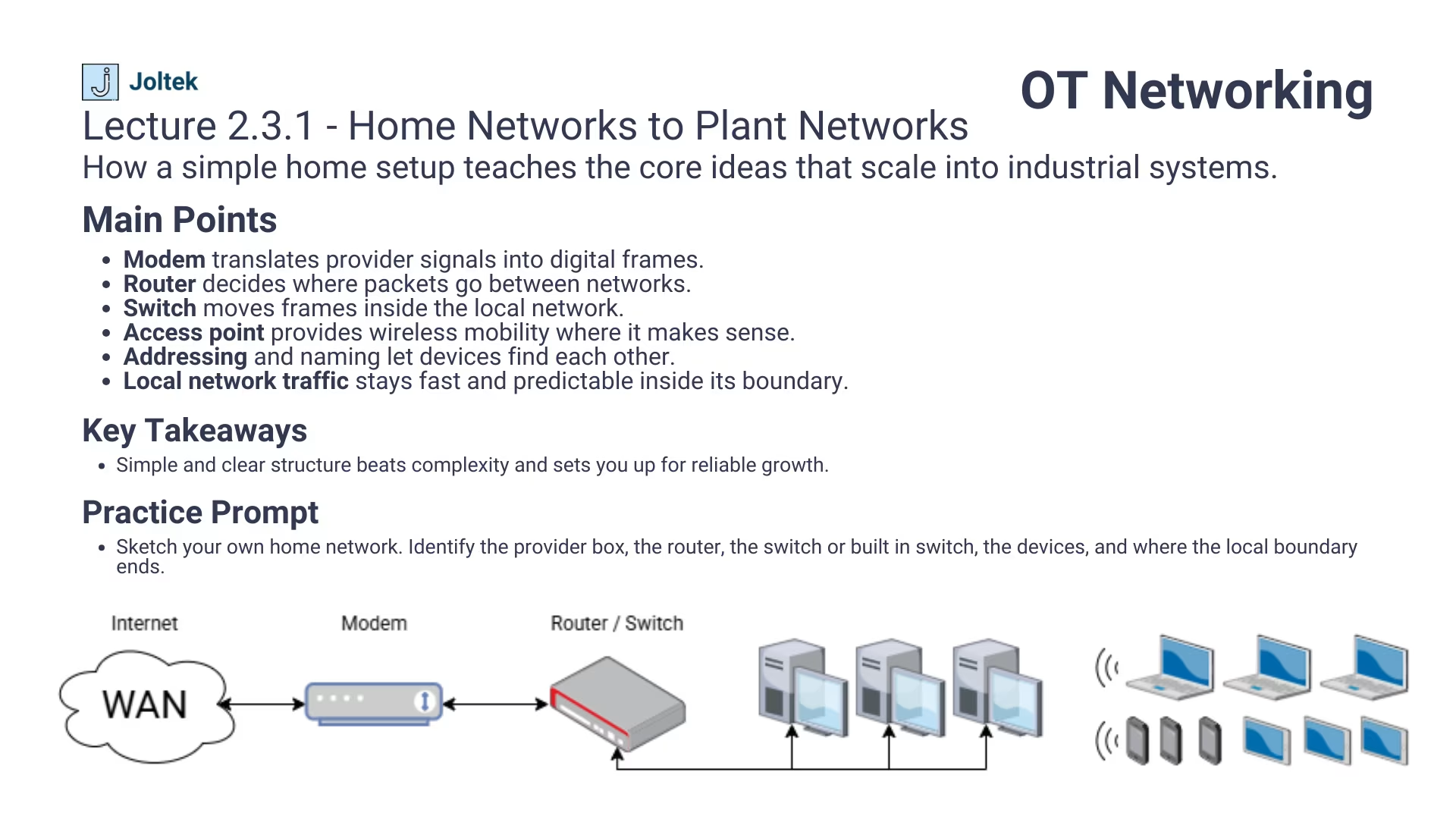
An Internet Service Provider, or ISP, is the company that delivers your connection to the internet. It is the invisible bridge between your local devices and the wider web. In your home, this might be a regional telecom provider. In a factory, the equivalent is the organization or infrastructure that connects the plant network to the corporate network or external systems such as cloud services.
In industrial environments, this external link might take several forms:
In both homes and industrial settings, the ISP or external gateway is the single entry and exit point for all data traffic. It defines how securely, quickly, and reliably information moves beyond local boundaries. Poorly configured connections can lead to downtime, security incidents, or unauthorized access. The same fundamental rules that govern your home internet apply to industrial networks, but the stakes are far higher.
For a detailed look at how industrial connectivity is expanding through modern platforms, explore Edge Solutions in Industrial Automation.
To understand how data travels between networks, we need to look at two core devices that every network relies on: the modem and the router.
A modem converts one type of signal into another. It receives data from the ISP as analog or optical signals and converts them into digital packets that can move across your internal network. The term modem comes from the words modulation and demodulation, which describe this process of encoding and decoding data for transmission.
A router takes the data received by the modem and decides where that information should go. It assigns IP addresses to connected devices and ensures that each message reaches the correct destination. In a home, the router typically handles both wired and wireless connections. It decides how your laptop, phone, and smart TV each access the internet through a single shared connection.
Modern consumer devices often combine both functions into a single box. However, in industrial settings, these components are more specialized and separated for better control and reliability. A plant network may use industrial routers, firewalls, and managed switches to create multiple layers of security and segmentation. This separation allows engineers to protect critical control systems from unnecessary exposure while still enabling controlled data exchange.
In manufacturing environments, physical and logical separation is not a luxury but a requirement for safety, uptime, and security.
When you understand how a simple home modem and router pair functions, you can better grasp the structure of industrial communication systems. The difference is that plant networks must ensure deterministic communication, redundancy, and resilience under demanding conditions.
To see how these foundational concepts scale into complete industrial architectures, read Manufacturing Concepts: Edge Devices, PLCs, IPCs, and Industrial Automation Architectures.
Every modern network can be divided into two broad categories: what happens locally and what happens across long distances. Understanding the difference between these two layers is essential before moving into industrial architectures. The relationship between the Local Area Network and the Wide Area Network determines how data travels from the factory floor to the enterprise level.
In consumer terms, this is the difference between devices communicating inside your home and data being sent to the internet. In industrial systems, it is the difference between machines talking to each other in a production cell and data being exchanged with business applications or cloud platforms.
A Wide Area Network, or WAN, connects local systems to external destinations. It is the bridge between your private network and everything outside of it. In a home, this means connecting your router to the internet. In a plant, this means connecting the factory network to corporate infrastructure, remote data centers, or cloud services.
The WAN is what allows organizations to centralize their data and access production information from multiple facilities. It is what makes global manufacturing visibility possible. However, the design of a WAN connection in an operational setting must account for very different priorities compared to traditional IT environments.
Industrial use cases of WAN connectivity include:
Each of these use cases introduces unique challenges in latency, reliability, and security. Unlike an office network, a delay of even a few milliseconds in an industrial setting can disrupt production processes or impact quality. Networks designed for operations must be deterministic, meaning that communication happens predictably and within strict timing requirements.
Security is also a critical consideration. Every connection to the outside world becomes a potential entry point for cyber threats. This is why OT networks often use industrial firewalls and segmented gateways to tightly control WAN access. The goal is to balance connectivity with protection, ensuring that critical systems remain isolated from external risk.
For a deeper look at how secure connectivity and data flow can be implemented across plants and enterprises, read Industrial Cybersecurity in Manufacturing.
A Local Area Network, or LAN, represents the group of devices that communicate within a specific location or environment. In a home, this might include your laptop, television, and smart speaker. In a plant, it includes PLCs, HMIs, SCADA servers, robots, and sensors working together to execute a production process.
Within a LAN, devices communicate at high speed through Ethernet connections or industrial switches. This environment is typically private and isolated from external networks, allowing for faster communication and greater control.
In manufacturing, LANs often mirror the physical structure of the facility:
To optimize performance and reliability, engineers often design LANs using segmentation and broadcast domains. A broadcast domain defines the group of devices that can communicate directly without routing. Limiting the size of this domain prevents network congestion and ensures that only relevant traffic flows where it is needed.
Understanding these local boundaries is essential before designing VLANs and subnets. Without this foundation, network segmentation can become inconsistent, leading to overlapping traffic or unintended communication paths. A well-structured LAN ensures that every device communicates efficiently, securely, and predictably within its intended environment.
To see how these principles evolve into advanced industrial architectures that balance performance and scalability, explore IT and OT Architecture Integration.
Every device on a network needs a clear identity in order to communicate. Think of it as a precise mailing address for data packets that must arrive at the correct destination without confusion. If you understand how addressing works, you can design plant networks that are predictable, secure, and easy to troubleshoot. For a deeper dive into how control systems move data once devices can see each other, read PLC Scan Cycles and SCADA Data Flow.
An Internet Protocol address is a numerical label that uniquely identifies a device on a network. Laptops, PLCs, HMIs, vision systems, and servers all use IP addresses to send and receive packets.
IPv4 uses four numbers separated by dots and is still the most common in OT environments. IPv6 uses a longer hexadecimal format that greatly expands the available address space. Many plants remain on IPv4 due to legacy systems and tooling, while gateways and firewalls can bridge to IPv6 where needed.
Private ranges are reserved for internal use and are not routable on the public internet. Typical choices in plants include:
Public addresses are assigned by providers and appear on the internet facing side of your network boundary.
Static addresses are manually set and remain fixed. They are preferred for PLCs, HMIs, historians, and servers that other systems must always find at the same location. Dynamic addresses are handed out automatically by a DHCP server and are common for laptops, tablets, and maintenance devices that come and go.
Routers often run a DHCP service that automatically gives an available address, a subnet mask, a default gateway, and DNS information to each client that requests it. This reduces manual work for noncritical endpoints.
Network Address Translation allows multiple private devices to share a single public facing address. When a device inside the plant initiates outbound communication, the router rewrites the source address to the public address and keeps a short state table so that replies return to the correct internal device.
NAT is widely used in manufacturing to isolate control networks while still allowing controlled outbound traffic for updates, telemetry, or secure remote access. It limits unsolicited inbound sessions and reduces the exposed surface of the plant.
Poor address management causes downtime and confusing failures. Duplicate addresses lead to intermittent communication. Incorrect gateways break access across subnets. Wrong masks create silent islands where devices cannot reach each other.
Adopt a simple and disciplined approach:
With these practices in place, you will prevent most network issues before they appear and create a foundation that scales cleanly as your plant grows.
Every useful network takes raw data from a source and moves it to a destination through a series of precise decisions made at different layers. Packets carry the payload while addresses and tables make sure each packet reaches the correct device with minimal delay. For broader architectural context around devices and data paths, explore Manufacturing Concepts: Edge Devices, PLCs, IPCs, and Industrial Automation Architectures.
When an application needs to send information, the system breaks the data into packets. Each packet gets headers that describe where it came from and where it is going. At Layer 2, the frame includes a source MAC address and a destination MAC address. At Layer 3, the packet includes a source IP address and a destination IP address. Switches make forwarding decisions based on MAC addresses. Routers make forwarding decisions based on IP networks and routing tables. Switches think locally in terms of MAC addresses while routers think globally in terms of IP networks.
Address Resolution Protocol answers a very basic question. I know the IP of the device I want to reach, what is its MAC address on this segment. A host broadcasts an ARP request asking who has a given IP. The owner replies with its MAC address. The sender stores the result in an ARP cache for a short time to avoid asking again immediately.
Older shared media networks could suffer collisions when two devices transmitted at the same time. Modern switched Ethernet isolates traffic into separate switch ports which prevents collisions and allows full duplex communication. Consumer gear still relies on basic switching and CSMA or CD rules where appropriate, while plant networks lean on quality of service, traffic engineering, and strict segmentation. Industrial systems depend on predictable timing which means the network must be engineered for consistent latency and bounded jitter.
Deterministic communication matters because controllers, drives, and safety systems expect updates within tight time windows. Common strategies include isolated VLANs for control traffic, priority queuing for critical frames, and selection of protocols designed for time awareness. Time sensitive networking features, scheduled traffic, and protocol level design choices help ensure that motion, safety, and synchronization do not contend with general traffic such as file transfers or maintenance laptops.
Home networks and plant networks share familiar building blocks, yet they serve very different goals. Convenience rules at home. Predictability rules in production. The way we design and govern the network must match the level of risk and the cost of downtime. For a deeper discussion of securing connected operations, read Industrial Cybersecurity in Manufacturing.
Consumer environments are designed for ease of use. A single device often combines modem, router, switch, and wireless access point. Devices appear and disappear without ceremony. DHCP quietly assigns addresses. Automatic updates run in the background. The experience feels invisible, which is exactly the point for a household. The essential idea is convenience first, where automation hides complexity so that devices just work.
Production environments demand reliability, uptime, and predictable timing. Engineers select hardware deliberately. Configurations are explicit. Redundancy is planned. Diagnostics are routine. The goal is to keep control traffic stable while the process runs without interruption.
In practice this means thoughtful choices and simple rules that everyone follows.
The defining principle is intentional control of every variable that can affect safety, quality, or throughput.
A home network trusts a simple secret. A plant network cannot. Access is granted based on role, location, and need. Wireless may be allowed for maintenance tools within a defined zone. Vendor access is time bound and audited. Firewalls enforce boundaries. Managed switches enforce who can talk to whom. Logs and alerts provide visibility that a household would never need.
Engineers use zoning to separate business services from operations, and operations from safety. They use segmentation so that only necessary paths exist. The result is a system that contains failure and resists intrusion while still delivering data to stakeholders who need it.
Security through segmentation is the core practice that keeps critical operations safe while allowing necessary connectivity.
Every healthy network relies on a small set of building blocks that move, isolate, and protect traffic. The right component choice and simple structure create predictable communication and easy troubleshooting.
A switch connects devices within the same local network and forwards frames based on MAC addresses. It learns which device is on which port and sends traffic only where it needs to go. A router makes decisions between networks based on IP subnets, while a switch focuses on local forwarding within one network. Think of the switch as the local traffic director and the router as the city planner that connects neighborhoods.
Unmanaged switches are plug and play with no configuration. They are suited for simple, low risk segments. Managed switches give you control over features such as port speed, spanning tree, mirroring, quality of service, and security settings. They also expose diagnostics that help you find errors before they become downtime. Managed switches let you shape traffic, enforce policy, and see problems early.
Virtual LANs create logical separation inside the same physical switch. They keep different kinds of traffic apart, reduce broadcast noise, and improve security. VLANs are the first step toward purposeful segmentation in plants and set the stage for clean routing between well defined zones. VLANs carve a single switch into tidy neighborhoods that only talk when you allow it.
At home, a wireless access point delivers convenience for phones, tablets, and laptops. It trades wire speed for mobility, which is perfect for casual use. In plants, wireless is best used where mobility is essential, such as maintenance tablets, warehouse scanners, or autonomous vehicles. For control loops and motion, wired links remain the default. Use wireless for mobility and noncritical workflows while keeping time sensitive control on copper or fiber.
A firewall enforces which traffic can pass between networks. At home, it blocks unsolicited inbound traffic and keeps devices safer by default. In industry, firewalls sit between business and operations, between operations and remote access, and at the plant edge. They filter by IP, port, service, and even by protocol content using deep packet inspection. Vendors offer industrial models that tolerate temperature, vibration, and electrical noise, such as platforms from Moxa, Hirschmann, and Stratix. Firewalls create the control points that turn a flat network into a governed system.
Inspection engines can recognize industrial protocols and apply precise rules. You can allow reads to a PLC while blocking writes, or permit historian collection while denying configuration changes. This turns connectivity into a safe utility rather than an open door. Protocol aware filtering lets you enable data sharing without exposing control.
Strong fundamentals make advanced design simpler and safer. When you understand the role of each component, configuration becomes a matter of applying clear rules.
Most troubleshooting reduces to checking the simple things first such as addressing, VLAN membership, and allowed paths. For an applied view of how these pieces fit together in real architectures, read Manufacturing Concepts: Edge Devices, PLCs, IPCs, and Industrial Automation Architectures.
A clear picture of how data moves gives you the confidence to build networks that are fast, resilient, and secure. The fundamentals you master at home translate directly to the plant floor. You now have the language to describe how devices identify themselves, how traffic stays local, and how it safely reaches external destinations.
Use a short exercise to turn concepts into muscle memory.
The same structure applies to PLCs, HMIs, SCADA, and MES. Fixed identities prevent confusion. Segmentation reduces noise. Firewalls and routing policies protect what matters while still enabling the right data to reach the right people. For an applied perspective on how these choices come together in real environments, read IT and OT Architecture Integration.
“In the next section, we will look at how industrial networks evolve from these fundamentals through segmentation, VLANs, and managed switch design.”